As AI technology continues to advance, traditional passwords may no longer be a secure way to protect sensitive information. With the added threat of quantum computing, even complex passwords could be easily broken in the near future. As a result, individuals and businesses should consider alternative methods for safeguarding their digital data.
The Problem with Passwords
Passwords, even when “strong”, present several challenges:
- Phishing Attacks: We’re giving away passwords without realizing it. As more and more the tech gets sophisticated, it benefits not just the good players, but also the bad players in the tech ecosystem. Phishing attacks are even getting advanced.
- Data Breaches: When the backends do not store passwords properly, massive leaks lead to our passwords being out in the open for hackers.
- Reused Passwords: This is common among many users. It’s tempting to reuse passwords across sites, creating a devastating domino effect if one site gets compromised.
So, how can we move towards a more secure way in the future?
Enter: The FIDO Alliance
The FIDO (Fast Identity Online) Alliance is a global industry association dedicated to solving these password problems. It’s a consortium of major tech companies, security experts, and more. Their mission is to replace our reliance on passwords with far more secure, user-friendly authentication standards.
Introduce: The Passkeys
FIDO introduced passkeys as an alternative to how we use passwords with MFA.
- No Passwords to Remember: Passkeys are unique digital credentials stored on the device (laptop, phone, etc.).
- Secured Locally: They’re never stored on a remote server, making them less vulnerable to data breaches.
- Cryptographic Proof: Passkeys use public-key cryptography—a complex mathematical method to verify your identity without transmitting a traditional password.
- Simple to Use: Unlocking with a passkey usually means a fingerprint scan, facial recognition, or a quick PIN on your device.
How are the private keys safe and why cant it be stealed?
This can be better understood if we understand how private keys are secured.
- No Central Storage: Unlike passwords that are often stored on company servers, private keys in the context of passkeys and cryptocurrency generally aren’t stored in any central database. They are either on the device or within specialized hardware.
- Encryption: Private keys are protected by strong encryption, making them difficult to decipher if accessed without authorization.
- Offline Storage (Cold Storage): For extra security, private keys can reside in offline devices (Something like ‘hardware wallets’) that are disconnected from the internet, making remote hacking nearly impossible.
- User Control: User is responsible for the security of the private keys. This means choosing secure storage methods and being careful about where and how the user use them.
It doesn’t mean that passkeys are 100% safe as well. Below are some of the areas where passkeys can still be vulnerable.
- Malware: If the device gets infected with malware specifically designed to steal private keys, they could be compromised
- Physical Theft: If someone physically steals the hardware wallet or device holding the private keys, and they are able to access its contents, the keys are at risk.
- Social Engineering: Hackers might trick user into revealing the private key or the seed phrase used to recover it through elaborate phishing scams.
- Poor User Practices: Storing the private keys in plaintext files, leaving the hardware wallet unattended, or clicking on suspicious links can make them vulnerable.
How does passkeys work?
Passkeys are still relatively new to the adoption. There are 2 major steps involved in passkey implementation are –
- Enrollment: The device generates a unique public-private key pair and registers the public key with the service.
- Authentication: The user authenticates themselves to their device (using a biometric or PIN) to unlock the private key, which is then used to sign a challenge from the service, verifying their identity.
Enrollment implementation can happen in 3 different ways –
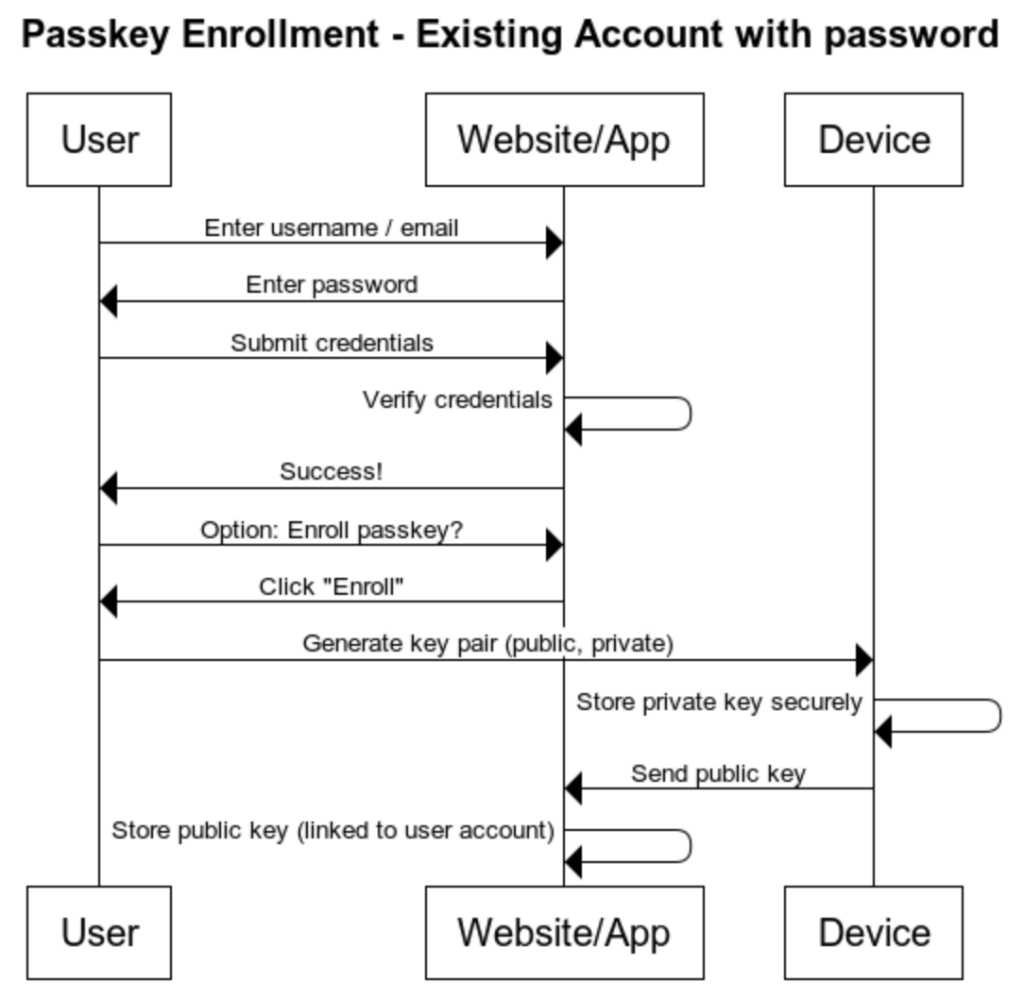
a. Existing account with password enrollment implementation
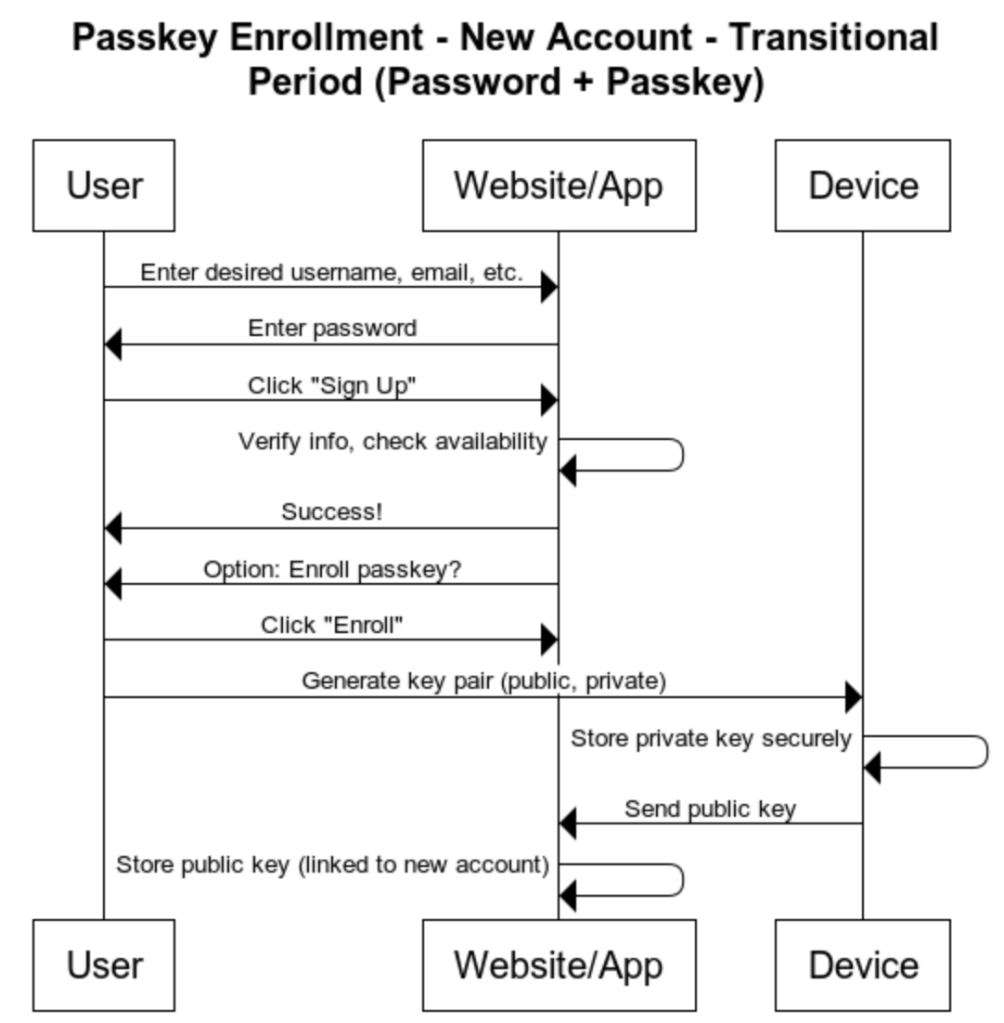
b. Passkey + Password Enrollment implementation
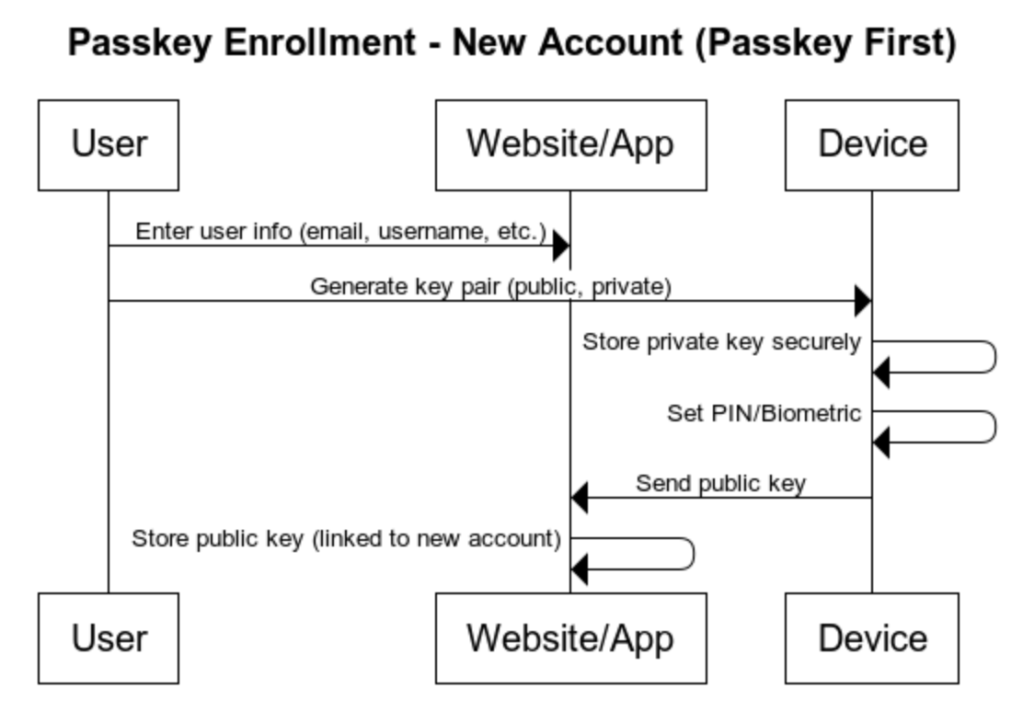
c. Passkey first enrollment implementation
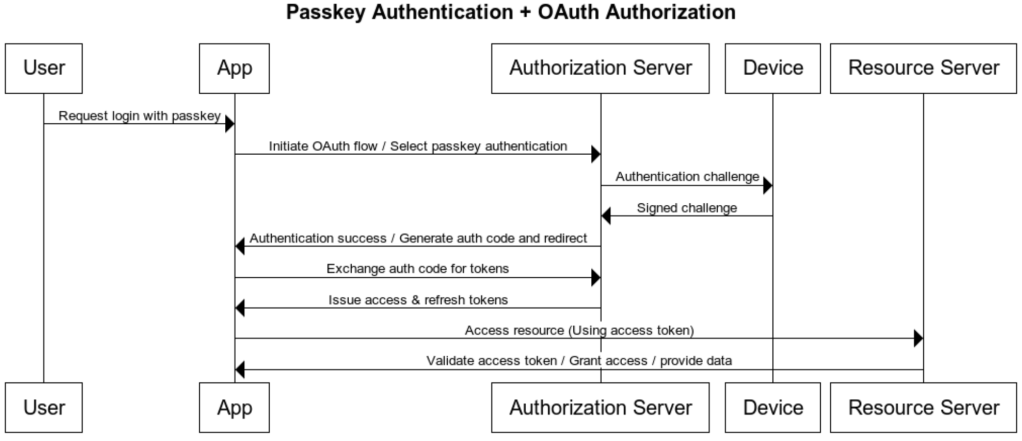
Passkeys authentication and authorization using oAuth2.0 –
Why is a password still relevant during the transitional phase?
A password is often still needed during the initial setup of a new account, even when opting to use passkeys:
- Fallback Authentication: Passkeys are relatively new. If something goes wrong during the setup, or you lose access to your device before enrolling a passkey, you need a way to recover your account. The initial password acts as a backup.
- Migration and Adoption: For websites with existing user bases, they can’t immediately force everyone to switch to passkeys. Passwords provide a familiar and universal login mechanism while passkey technology gains broader adoption.
- Multi-Device Strategies: While passkeys aim for cross-device compatibility, in the early stages it’s helpful to have a fallback mechanism to easily log into your new account from a different device where you haven’t yet set up your passkey.
- Account Verification: A password can help in the following ways:
- Email Verification: Combining a password with account creation allows for email-based account verification, reducing spam and fake accounts.
- Defense Against Bots: Requiring a password adds an obstacle for automated account creation attempts.
- Legacy System Compatibility: Some websites may have older systems in place that are heavily reliant on passwords. Integrating passkeys fully can take time, so a password might act as a bridge for security in the meantime.
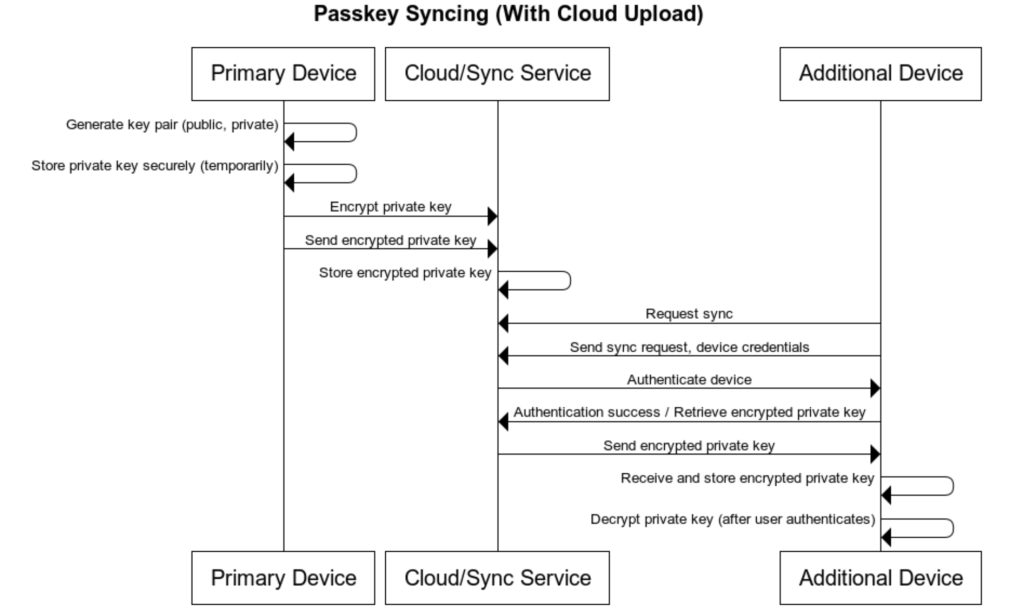
How to sync passkeys across devices?
Advantages of Passkeys:
- Hack-proof: Phishing attempts become practically useless, as there’s no password to steal!
- Breach-resistant: Even if a site is hacked, the data obtained wouldn’t help hackers access your account.
- Convenient: No more memorizing complex passwords or resetting them constantly.
The Future is Passwordless
FIDO, with support from giants like Google, Apple, and Microsoft, is making significant strides. Our devices are slowly but surely adopting passkey technology. This trend signals a more secure and convenient online experience, where passwords will eventually be a relic of the past.
Share your use case and strategy in migrating your application towards passkey based auth.
Happy learning!