Imagine a future where AI agents seamlessly handle tasks and transactions on our behalf. But how do we make sure these autonomous systems are acting responsibly and with proper authorization? Establishing trust and accountability in AI-driven interactions is a monumental challenge. We will look into how Verifiable Credentials are offering a crucial part of the solution. They enable secure and verifiable identities for the age of agentic AI.
Verifiable credentials (VCs) are emerging as a transformative technology in the area of digital identity. These digital representations of real-world credentials, such as passports or driver’s licenses, offer a secure and trustworthy way to prove identity and attributes online. As we move towards an era of agentic AI, where AI agents act autonomously on our behalf, VCs become even more critical in establishing trust and accountability. This blog post takes a closer look at verifiable credentials, exploring their potential to revolutionize how we manage and verify identities in the digital age, particularly in the context of agentic AI.
What is a Verifiable Credential?
Verifiable credentials are essentially digital credentials that adhere to open standards set by organizations like the World Wide Web Consortium (W3C). They can represent information found in physical credentials, such as a passport or license, as well as new things that have no physical equivalent, such as ownership of a bank account. In essence, VCs provide a standardized, digitally signed way to package claims about individuals, organizations, or other entities. These claims can range from simple assertions like “this person is over 18” to more complex statements like “this person holds a degree in computer science from this university.”
VCs also include important metadata that provides context and increases trust. This metadata might include the credential identifier, the issuer of the credential, the date of issuance, and the credential’s expiration date. This metadata, often cryptographically signed by the issuer, helps to ensure the credential’s authenticity and validity.

Verifiable Credentials vs. Identity Tokens
While both verifiable credentials and identity tokens play a role in digital identity, they have different purposes and characteristics.
VCs vs. Identity Tokens
Identity tokens, like those used in OAuth 2.0, are primarily used for authentication. They verify that a user is who they claim to be when accessing a service. These tokens are typically short-lived and contain limited information about the user.
Verifiable credentials, on the other hand, are designed for broader use cases beyond authentication. They can represent a wide range of attributes, such as educational qualifications, professional certifications, or even proof of age. VCs offer greater flexibility and control over what information is shared. For example, someone could share their license certification number to prove their qualifications without revealing their full address or other personal details.
VCs vs. NFTs and SBTs
VCs also differ from other digital tokens like Non-Fungible Tokens (NFTs). While NFTs are often publicly viewable and represent ownership of unique assets, VCs are associated with Decentralized Identifiers (DIDs) and are not publicly viewable. They are selectively shared with verifying parties as needed, ensuring greater control over personal data.
It’s also important to distinguish VCs from Soulbound Tokens (SBTs). SBTs are a type of non-transferable token that is permanently tied to a specific wallet address. While they have potential for use in identity, they carry the risk of making private information public, unlike VCs, which prioritize privacy and selective disclosure.
One of the key advantages of VCs is that they empower users with greater control over their data. In a world where data is increasingly valuable and personal information is often shared without our full understanding or consent, VCs offer a way to regain control and make informed decisions about what information we share and with whom.
How Verifiable Credentials Work?
The VC ecosystem involves three main entities:
- Issuer: The trusted entity that creates and issues the VC. This could be a government agency, educational institution, or even a private company.
- Holder: The individual or organization that receives and stores the VC. Holders typically store their VCs in a digital wallet.
- Verifier: The entity that requests and verifies the VC. This could be an employer, service provider, or any other party that needs to verify information about the holder.
The process typically starts with the holder requesting a credential from the issuer. The issuer then generates a digital credential that includes information about the holder and the credential itself, such as its type, issuer, issuance date, and expiry date. The issuer digitally signs the VC with their private key and sends it to the holder, who stores it in a digital wallet.
When the holder needs to present the credential to a verifier, they generate a verifiable presentation (VP). A VP is a secure way to present data from one or more VCs to a verifier. VPs allow holders to selectively disclose only the necessary information, further protecting their privacy. The verifier then retrieves the public keys of the subject and the issuer from a trusted source, known as the Verifiable Data Registry, and uses cryptographic techniques to verify the authenticity and validity of the VC.
A crucial aspect of this process is the use of Decentralized Identifiers (DIDs). DIDs are unique identifiers that are linked to individuals or entities. They are used in VCs to establish a verifiable link between the holder and their credentials, ensuring that the credentials can be trusted and attributed to the correct individual.
To ensure the structural integrity of VCs and enable consistent interpretation of the data, JSON schemas are used. These schemas provide a standardized way to define the structure and content of VCs, making it easier for issuers, holders, and verifiers to understand and trust the information they contain.

Where are Verifiable Credentials Used Today?
Verifiable credentials are already being used in a variety of sectors, including:
- Education: Educational institutions are issuing digital diplomas and certificates that can be easily verified by employers. This streamlines the process of verifying qualifications and reduces the risk of fraud.
- Government: Governments are using VCs for digital identity cards, driver’s licenses, and other official documents. In this context, government agencies act as “trust anchors,” entities that issue VCs, increasing the trustworthiness of the credentials. This can simplify interactions with government services and improve efficiency.
- Healthcare: VCs are being used to represent health records, vaccination records, and other sensitive medical information. This can empower patients with greater control over their health data and facilitate secure sharing of information with healthcare providers.
- Finance: Banks are using VCs to streamline KYC processes and provide secure access to financial services. This can reduce onboarding time for new customers and improve the overall customer experience.
These are just a few examples of how VCs are being used today. As the technology matures and adoption grows, we can expect to see even more innovative use cases emerge. VCs have the potential to streamline and automate various processes, such as KYC in finance or employee onboarding, leading to increased efficiency and reduced costs. They also create new business models and revenue streams, particularly for “trust anchors” who verify information.
How Verifiable Credentials Make Use of Blockchains?
Blockchain technology plays a crucial role in the VC ecosystem by providing a secure and tamper-proof way to store and manage DIDs and credential schemas. The decentralized nature of blockchain ensures that no single entity controls the system, making it more resilient to fraud and censorship.
Blockchains can be used to record the issuance and revocation of VCs, providing an auditable history of credential status. This helps to prevent fraud and ensures that only valid credentials are accepted by verifiers.
Furthermore, blockchain technology enables “cross-chain verification,” allowing VCs issued on one blockchain to be verified on another. This enhances the interoperability and flexibility of VCs, making them more widely applicable across different platforms and systems.
Zero-Knowledge Proofs (ZKPs) are another important aspect of how VCs leverage blockchain technology. ZKPs allow holders to prove aspects of their credentials without revealing the entire credential. This enhances privacy and security, as only the minimum necessary information is shared with verifiers.
Verifiable Credentials and Agentic AI: A Perfect Match
Agentic AI, with its ability to act autonomously and make decisions, presents new challenges for identity management. How do we ensure that AI agents are who they claim to be and have the necessary permissions to perform their tasks? This is where VCs come in.
VCs can be used to provide AI agents with verifiable identities, allowing them to authenticate themselves and prove their capabilities to other agents and systems. This is crucial for establishing trust and accountability in AI-driven interactions.
For example, an AI agent acting on behalf of a user could present a VC to prove that it has been authorized by the user to perform a specific task. This helps to prevent unauthorized access and ensures that AI agents operate within defined boundaries.
VCs can also help to mitigate bias and discrimination in AI systems. By providing verifiable evidence of ethical compliance, VCs can increase trust in AI systems and ensure that they are used responsibly.
It’s important to consider the different types of AI agents and how VCs can be applied to each type. AI agents can range from simple bots with limited autonomy to sophisticated assistants that can perform complex tasks. The level of autonomy and the capabilities of the AI agent will influence the type of VCs needed and how they are used.
Architecture for Agentic AI with Verifiable Credentials
To effectively utilize VCs with agentic AI, a robust architecture is needed. This architecture should address key aspects such as identity management, authentication, authorization, and auditability.
Here’s a possible architecture:
- Decentralized Identifiers (DIDs): Each AI agent is assigned a unique DID, providing a verifiable and persistent identity.
- Verifiable Credential Issuance: Trusted authorities issue VCs to AI agents, containing claims about their capabilities, permissions, and other relevant attributes.
- Credential Wallet: AI agents store their VCs in a secure digital wallet, allowing them to manage and present credentials as needed.
- Authentication and Authorization: AI agents use their VCs to authenticate themselves to other agents and systems, proving their identity and authorization to access resources or perform actions.
- Ephemeral Credentials: For enhanced security, AI agents can generate ephemeral VCs that are valid only for a specific task or time period.
- Auditability: All actions taken by AI agents are logged and linked to their DIDs, creating an auditable trail for accountability and compliance.
This architecture ensures that AI agents operate securely and transparently, with clear accountability for their actions.

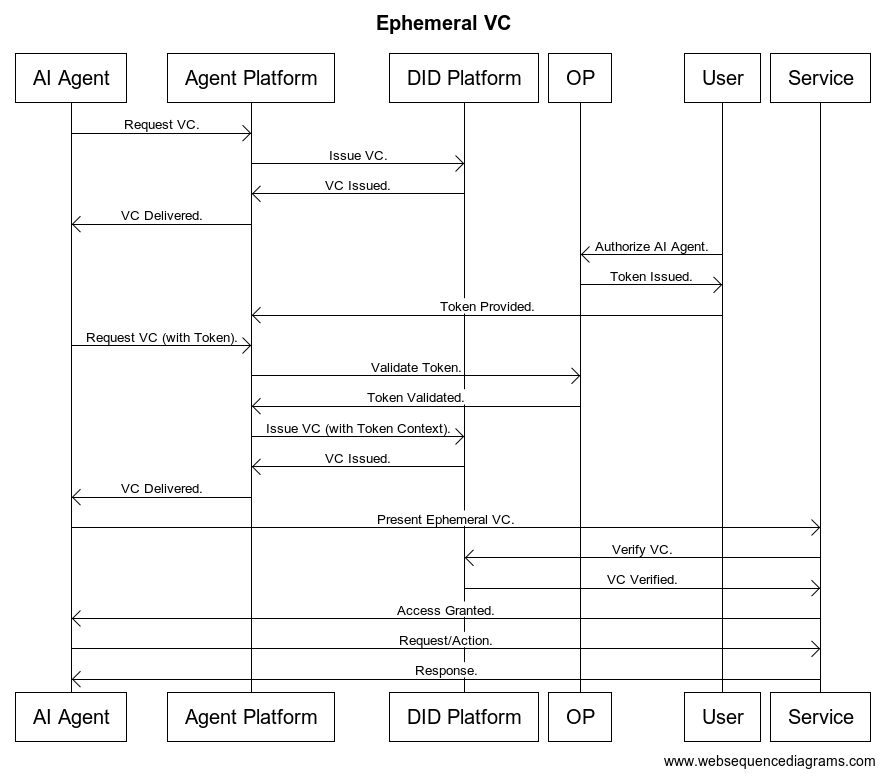
Generating Ephemeral Verifiable Credentials
Generating ephemeral VCs for AI agents requires a system that can issue credentials on demand with specific validity periods and attributes. This could involve integrating VC issuance capabilities into the AI agent platform or utilizing a dedicated credential issuance service.
One approach is to use a decentralized identity platform that supports the issuance of short-lived VCs with fine-grained access control. This allows AI agents to request and receive credentials with the specific permissions they need to perform a task, ensuring that their access is limited and temporary.
This process can be further enhanced by leveraging OpenID Providers (OPs) and delegation tokens. OPs act as trusted entities that issue and validate credentials for AI agents. Delegation tokens, issued by human users, authorize AI agents to act on their behalf within defined boundaries.
Benefits and Challenges of Verifiable Credentials for Agentic AI
Verifiable credentials (VCs) offer a powerful approach to managing and verifying the identities of agentic AI, but their adoption comes with both benefits and challenges.
Benefits
- Enhanced Privacy: VCs empower users and AI agents with greater control over their data by enabling selective disclosure. This means they can share only the necessary information for a given interaction, mitigating concerns about centralized logging and cross-platform correlation inherent in traditional architectures like OpenID Connect (OIDC).
- Decentralization: Unlike OIDC, which relies on a central OpenID Provider (OP), VCs are not bound to a specific transport protocol and can be presented and verified in a decentralized manner. This reduces reliance on a single identity provider and enhances flexibility.
- Improved Security: VCs are tamper-evident and cryptographically secure, making them more trustworthy than traditional credentials. This is crucial for establishing trust and accountability in AI-driven interactions.
- Interoperability: VCs adhere to open standards, ensuring compatibility across different platforms and systems. This facilitates seamless verification and interaction between AI agents and various services.
- Trust and Accountability: By providing verifiable identities and attributes, VCs enhance trust in AI agents and their actions. This is essential for responsible and ethical AI development and deployment.
- Reduced Costs and Increased Efficiency: VCs can streamline processes like authentication and authorization, leading to cost savings and increased efficiency.
Challenges
- Ecosystem Maturity: While VCs are gaining traction, the ecosystem is still developing compared to the mature OIDC ecosystem. This means there’s less readily available tooling and infrastructure for managing VCs at scale.
- Scalability: Verifying VCs can be computationally intensive, especially if each verification requires a new signature check or interaction with a blockchain. This presents scalability challenges as the number of AI agents and interactions grows.
- Integration with Existing Systems: Integrating VCs with existing identity and access management systems can be complex. Organizations may need to adapt their infrastructure to accommodate VCs, which can require significant effort and investment.
- Standardization: While VCs adhere to open standards, there is still ongoing work to ensure consistent implementation and interoperability across different platforms and use cases.
Despite these challenges, the benefits of VCs for agentic AI are significant. As the technology matures and adoption grows, we can expect to see solutions that address these challenges and unlock the full potential of VCs for secure and trustworthy AI interactions.
Please share your thoughts and insights on how to best leverage VCs to ensure secure and trustworthy interactions with agentic AI. How would you approach the implementation of VCs in your own organization or projects? What solutions do you envision for addressing the challenges of authentication and authorization in the age of agentic AI?
Happy Learning!
One thought on “Verifiable Credentials: A Deep Dive for the Agentic AI Era”